The African market has experienced major changes in building security over the years. According to Mr. Muhammed of Crown Hyper a world renowned company, that provides premium brand products in the field of Electronics and IT in South Africa, the market is now open to innovation and it is a place that closely follows technology; therefore projects are taking place based on standards preferred by investors. The best products produced in countries like Turkey and France, are brought to Africa where the projects are. As a matter of fact, many international companies carry out production and testing in Africa. Therefore, many technological developments are spreading from Africa to the rest of the world.
Building Monitoring
The way to achieve efficient monitoring is by installing an integrated system, this is according to Mr. Cem Atam of Kekova a security consulting firm in Turkey. It is possible to control the system with a single center (more than one spare structure according to need) and less hardware. This will reduce both operational and maintenance costs, increasing your business strength, enabling you to increase profitability in your business and have a long-lived facility.
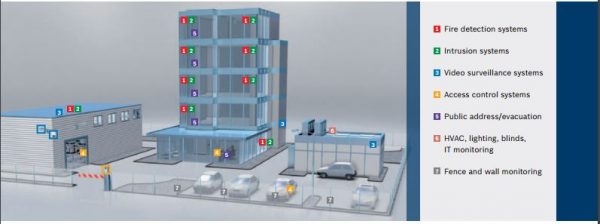 “The Turks have a proverb; “from being one, strength is born.” In other words, we should think of our facilities as a living organism; we have to follow every functioning or stationary point and watch the changes. This plays an important role both in terms of security vulnerabilities and control of the system’s good operability,” he says.
“The Turks have a proverb; “from being one, strength is born.” In other words, we should think of our facilities as a living organism; we have to follow every functioning or stationary point and watch the changes. This plays an important role both in terms of security vulnerabilities and control of the system’s good operability,” he says.
Also Read:Fire safety in buildings
Documentation of security matters
Every client has unique documentation requirements for their project. Depending on the type of facility and the regulations, codes, construction and service technical information required, the extent of required or requested documentation can vary radically. In the design and engineering stage, this may mean submittals to authorities, architects, owners or other stakeholders. Proper process and form for this type of documentation matters.
The security designers should possess the ability to create specialized output of documentation. This include electronic forms such as AutoCad, Building Information Management (BIM) or other systems. The consultant should work with you to design the documentation package that you require, from design, to construction and to post-delivery support.
According to Sibusiso Dhlamini the Sales and Marketing Executive at Tagtron Solutions a specialist in EAS and RFID solutions offering a range of hardware security equipment in Sub Saharan Africa the best way to document data is to have it done automatically using software. If you are using RFID, simply saving the RFIDs ID number with a timestamp in a database saved to the cloud is all you need. Then you can analyze the data at a later stage. As long as you have the data you can always compile new reports from it.
“We find that most companies are doing a shift to cloud computing where the data is not stored locally on a hard drive but in secure servers all over the world. This means if your company burns down or a virus deletes everything your data is still secure. Most cloud servers can even back track stored data for a few months meaning that even if someone deleted all your data on the cloud you could still recover everything,” he adds.
Government policies
Governments in most manufacturing countries have formed commissions to provide regulations and standards in the market. Manufacturers develop products that meet these standards to ensure quality and good service. These commissions include: the European standards committee (CEN), British Standards Institution (Bsi) and Turkish Standards Institution (TSE), National Institute of Standards and Technology (NIST) etc.
These commissions document matters with regards to: information security, durability, energy consumption, carbon emissions, etc. Some of these certifications can be taken during the production phase and during the usage phase. For example, like a LEED certificate.
Considering the importance of these commissions, Mr. Atam advises that, it is paramount to develop policies that follow technological developments, overlap with life and regional conditions, and have vision.
Choosing the right security system
Generally, most countries have institutions that formulate certain standards by which the products in the market are usually shaped within. These standards are generally based on regulations or standards of neighboring countries and producing countries.
When it comes to choosing the right product, it is very important to talk to experts in the field. “It is highly advisable to meet with a few consulting firms and present your ideas or vision, then go for the best system. The choice that you make should be guided by your expectations for tomorrow, not today. This means that the products should have a low failure rate, a large service network and low operational and maintenance costs. Moreover, the consumer should ensure that the product is certified regardless of the price; a certified system has passed many tests and has a good design,” asserts Mr. Atam.
Nevertheless, Mr. Albert Abincha, a Business Executive at Cathexis Technologies a leading IP Video Management Software Developer, specializing in Surveillance Solutions for the international market in South Africa mentions that, the consumers of security services are not only becoming savvier to technological changes but are also seeing the value in consulting with skilled installers and integrators who can provide them with the best consultation on the right type of system for their operations.
According to George Mutai a Sales Engineer of South Africa’s Axis Communications, a leader in network video; by coming up with a needs analysis, finding the right partners and following best-practice. The selected solution should be able to address the needs that the client wants addressed.

Security systems always be good 🙂 Thank you